IAM Roles for Amazon S3
Why Are IAM Roles Used?
An IAM role is an IAM identity that has specific permissions. Roles can be used to delegate access to users, applications, or services to access specific AWS resources. For example, to grant users access to resources they don’t usually have, or grant users in one AWS account access to resources in another account.
Using IAM Roles in Transmit
When connecting to S3 with an IAM role, there are additional fields to fill in.
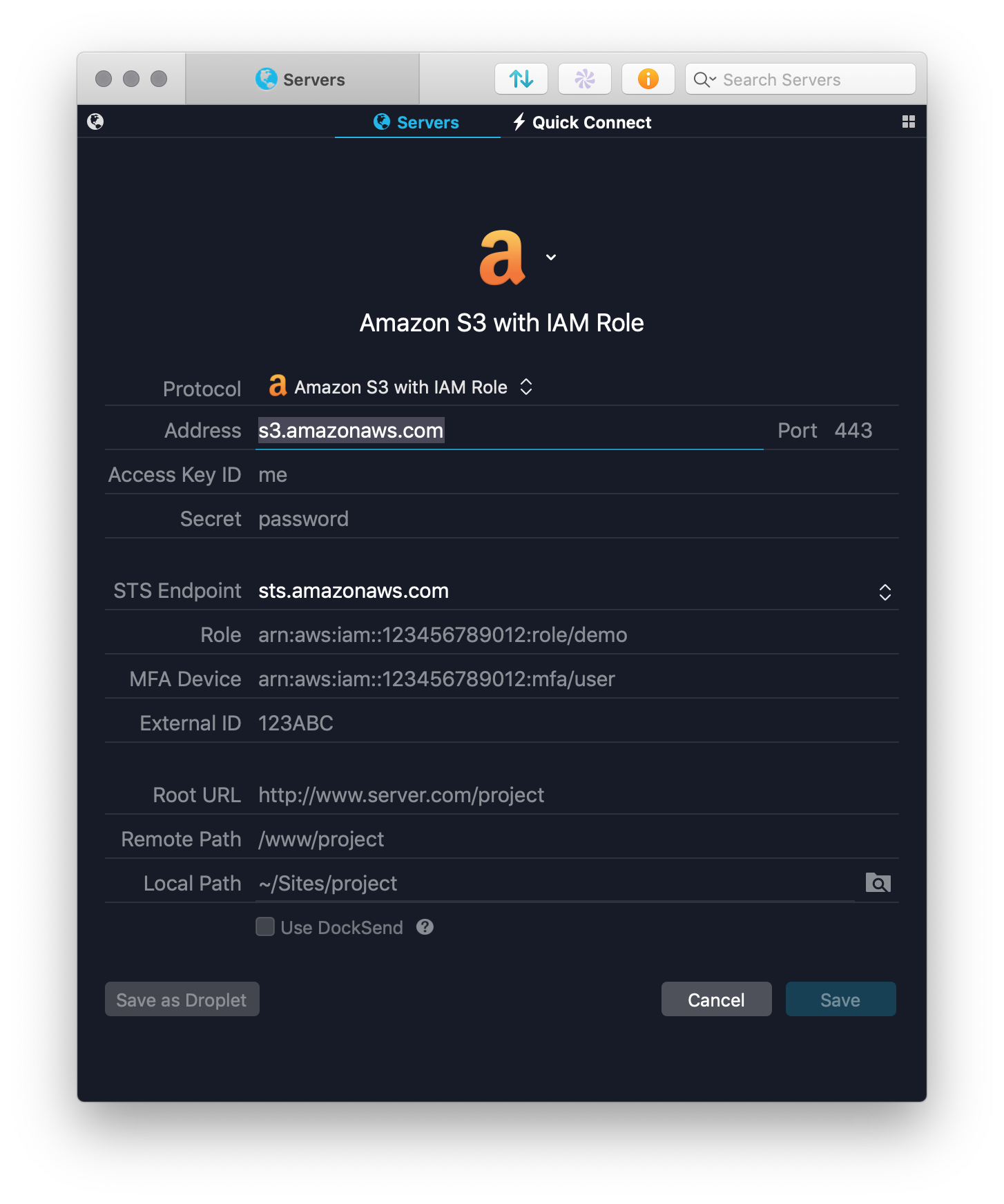
The Address, Access Key ID, and Secret fields are the same as with regular AWS logins. These fields are the permanent credentials for the IAM user, and not the temporary credentials for the IAM Role.
The STS Endpoint field defaults to sts.amazonaws.com. If necessary, the STS endpoint can be set to a specific region, and Amazon maintains a list of supported endpoints.
The Role field is required, and provided by your AWS administrator. If you’re unsure what role to specify, please speak with your admin.
The MFA Device field is optional and should only be filled in if your account requires 2FA. When this field is filled in, Transmit will prompt for a 2FA code when connecting.
If 2FA is required for this account, but this field is left empty, S3 will return a generic
Access Deniederror. It will not indicate that 2FA is required for the account. If you see an access denied error when attempting to connect, check to see if the account requires 2FA.
Finally, the External ID field is optional. This is usually used by administrators to link AWS roles to external auditing systems.
If your administrator requires an external ID, Transmit will display the same generic
Access Deniederror.
Restrictions
Currently Amazon S3 with IAM Role based servers are not supported for use with Transmit’s Automator actions.
Active Directory and OpenID Authentication
Transmit does not currently support assuming IAM roles using OpenID or SAML. If this is something you’d like to see in a future version of Transmit please contact us to provide more information about your specific use-case.
Configuring IAM roles for S3
IAM role configuration and managment can only be performed via the S3 console.
If you have questions or issues concerning IAM role configuration please contact AWS support for assistance.